In computer science, cryptography is a method of hiding information in storage and during communication so that only authorized people can access that information. Cryptography contains a lot of cryptology methods for securing communication and information like hiding text or messages behind images, Asymmetric encryption (public key cryptography) for securing Networks. In this article, we are going to discuss some common and popular cryptography tools and techniques.
Steganography
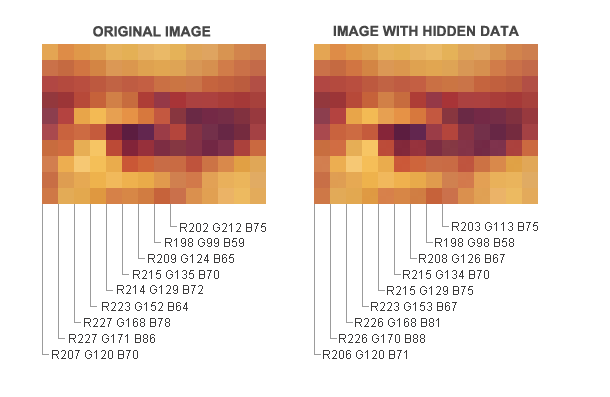
Steganography is a method of hiding information, messages, or files behind an image especially from the people who could snoop on our messages. A picture file contains some unused space in it and that space can be used for storing messages or some information in it. The good part is, a snooper would have no idea that the picture has some hidden information in it.
Recommend tool: You can use LSB-Steganography for hiding files into an image which is an open-source software program for steganography.
Rot13
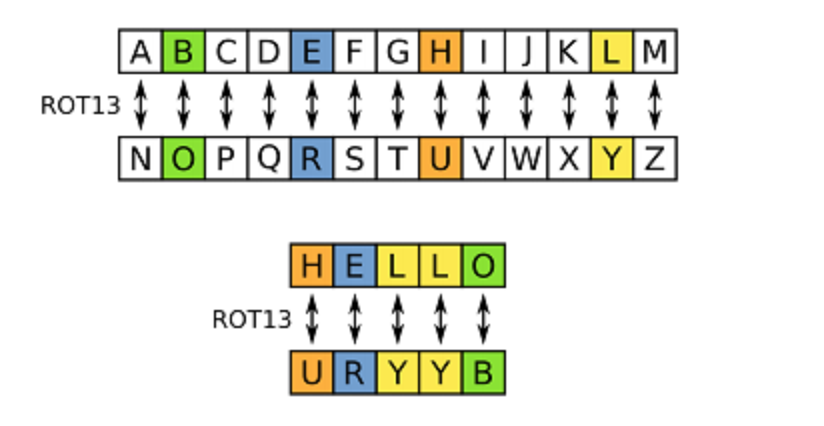
Rot13 or Rotated by 13 is a simple cryptography system where the first letter of a word gets replaced with the 13 letters down the alphabet as there are 26 letters alphabet so the algorithm that encodes the message also decodes it. We can also use Rot12, Rot14, and a lot of other Rot ciphers.
Recommend tool: There are lots of sites that provide Rot13 encode and decode service which you can use I would recommend using Rot13.com to use.
Secure Shell
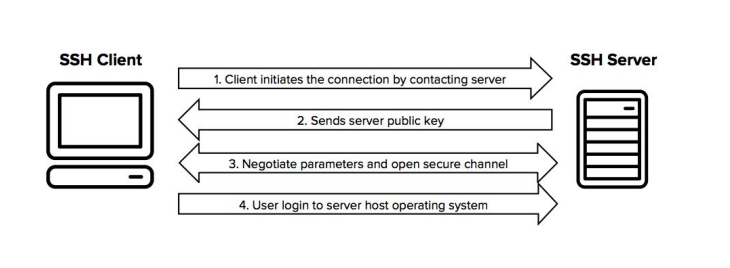
Secure shell provides secure communication by securing a network. It is a cryptographic network protocol so that you can secure your communication over an insecure connection. The most common use of this protocol is in remote login services where the connection is encrypted with a secure shell so that no third party can snoop on the password in that network. Secure shell is also used for secure file transfer which Secure File Transfer Protocol (SFTP). SFTP is a subsystem of a secure shell for handling file transfer, some advantage of SFTP is it encrypts username as well as password and the file which is being transferred over that network.
Recommend Tool: There are a lot of applications for secure shell but I will provide IronSFTP which is an open-source program for Secure end-to-end encrypted file sharing over a secure shell.
Author: Shaquib Izhar, Cyber Security Researcher, and Ethical hacking Trainer.

