This is how easy to phish someone with good Social engineering Techniques
It’s been a while since I posted my last post. So I decided to do a quick write-up on social engineering attacks. I will show how easy it is to phish someone using a Good social engineering attack. I will try to make this post-noob-friendly to prove that how easy it is for anyone with good social engineering skills but with little to zero technical knowledge can phish a user. Even though I am not an expert at soc engineering I was able to take down some accounts.
Attack scenario
This time I decide to attack random people, this was to see how difficult or easy it to phish some random people.
Preparing the Attack
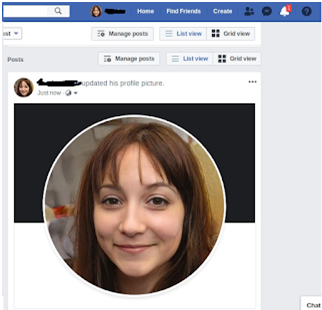
First I need to make a fake Facebook profile and it’s better to not use those type of profile which could be easily reverse search like some celebrity photo etc, so I used “thispersondoesnotexist.com” which generate fake person pic using AI techniques every time you refresh the page, so it would be good the choice for making this type of fake profiles. As shown below I decided to choose the below pic which looks easy to convince people.
I updated the profile pic.
Pic 1: Create a profile
Then I sent a friend request to some girl’s profile, this can make it easy to lure the target if a girl’s profile has more female friends than any male that will look more legit.
Pic 2: Sent Friend Request
Then I got some requests from some male profiles and also got comments on my profile pic.
Pic 3: Comments Over profile Pic
I decided to wait so that one of them start conversion with me and after some time I got a message from both of them.
Pic 4: Getting Messages
I did some usual chat with both of them for some time, I did not reply immediately to their message when I was AFK. After some long conversation, when they will get comfortable with the fake person, I will ask them to do a favor
Pic 5: More Messages Building Trust
Preparing The Attack
This time I decided to use automation for this phishing attack, this can save some time also. For the attack, I am going to use socialphish this comes with some phishing templates and also with ngrok as my current target isn’t techie this time this is a good choice for tunneling.
“I installed it”
Pic 6: Preparing Attack
And after running it gave me choices of what type of template I want to use.
Pic 7: Option in the tool
I chose the first template FbRobotCaptcha on visiting this page will ask to prove if the person is not some bot which looks like as shown below.
Pic 8: Choose Selection 1
Visiting the page will show something like this
Pic 9: Verification Image
Now when the user will choose login with FB it will get redirected to the Facebook login page as shown below
Pic 10: Login page
Now on after submitting the password, the user will be redirected to the URL shown below
Pic 11: Error 404
Now the server is up and it’s time to send the link
Pic 12: Attack Prepared
Sending The link
The first target seems to get offended by asking about his career so I move on to the second target and ask him to do me a favor
Pic 13: Got a message from Victim
Then I told him how to sign up for this petition and then sent the short link.
Pic 14: Another Message
Pic 15
Now I waited for him to make the login attempt and after some minutes I got the credentials.
Pic 16
Final words
Above article proof that doesn’t believe everything you see online second never open any link without complete verification by scanning on virustotal or urlscan.io which is send by some stranger.